Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
%term
How to Get Involved in Cybersecurity with Lidia Giuliano
Survey: 93% of ICS Pros Fear Digital Attacks Will Affect Operations
Digital attackers are increasingly targeting industrial environments these days. Take manufacturing organizations, for instance. Back in late-August, FortiGuard Labs discovered a malspam campaign that had targeted a large U.S. manufacturing company with a variant of the LokiBot infostealer family. It wasn’t long thereafter when Bloomberg reported on the efforts of bad actors to target Airbus by infiltrating its suppliers’ networks.
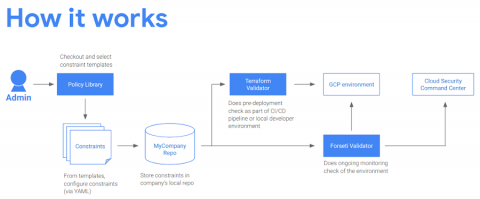
Protecting your GCP infrastructure at scale with Forseti Config Validator part two: Scanning for labels
Welcome back to our series on best practices for managing and securing your Google Cloud infrastructure at scale. In a previous post, we talked about how to use the open-source tools Forseti and Config Validator to scan for non-compliant tools in your environment. Today, we’ll go one step further and show you another best practice for security operations: the systematic use of labels.
Tracking Malicious Activity across the Sumo Attack Lifecycle
Knowledge Management with Netwrix Data Classification
6 Common Phishing Attacks and How to Protect Against Them
Phishing attacks don’t show any sign of slowing down. Per its 2019 Phishing Trends and Intelligence Report, PhishLabs found that total phishing volume rose 40.9 percent over the course of 2018. These attacks targeted a range of organizations, especially financial service companies, email and online service providers and cloud/file hosting firms.
Key tips to finish your 2019 cyber year strong and prepare for 2020
As we quickly approach the last quarter of the year, it's a good time to reflect on what's happened thus far in 2019, and where we should focus our energy for 2020.
Secure Configuration in Cloud - IaaS, PaaS and SaaS Explained
If I asked you what security products you had in place to manage your risk within your IT organisation 10 years ago, you’d probably have been able to list a half dozen different tools and confidently note that most of your infrastructure was covered by a common set of key products such as antivirus, DLP, firewalls, etc. But in a world with IaaS, PaaS and SaaS, maintaining a comprehensive approach becomes far more difficult.
Automating Secure Configuration Management in the Cloud
For many organizations moving to the cloud, Infrastructure as a Service (IaaS) like AWS EC2, Azure Virtual Machines or Google Compute Engine often forms the backbone of their cloud architecture. These services allow you to create instances of pretty much any operating system almost instantly. Unfortunately, moving your IT infrastructure to the cloud doesn’t relieve you of your compliance or security obligations.