Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
%term
What is a Computer Worm?
A computer worm is a type of malicious software that self-replicates, infecting other computers while remaining active on infected systems. Worms can often go unnoticed until their uncontrolled replication process consumes system resources, halting or slowing the infected computer. Along with computing resources, networks can become congested by traffic associated with worm propagation.
The Future of Cybersecurity Insurance
Cybersecurity incidents and data breaches have become a normal part of the news cycle. It feels like every day you hear about a big corporation or organization suffering an attack that has put customer or user data in jeopardy. Sometimes this is because a security strategy was lacking; sometimes, the criminal’s attack was simply too powerful. Regardless of how or why a cyberattack begins, the fallout can be devastating for all those involved.
What are Defence in Depth Measures?
Defence in depth is an approach to IA. It derives its inspiration from the military strategy with the same name. In this article, we explained what defence in depth involves and why it is useful for your organization.
Detectify secures 21,5 million in Series B round to bring world-class cyber security to everyone
Stockholm, Sweden. November 26, 2019 – Detectify, today announces a successful Series B round of €21,5 million led by venture capital firm Balderton Capital, and supported by existing investors Paua Ventures, Inventure and Insight Partners. The new funding will be used to continue to hire world-class talent to further accelerate the company’s growth and deliver on Detectify’s promise of a safer internet for all.
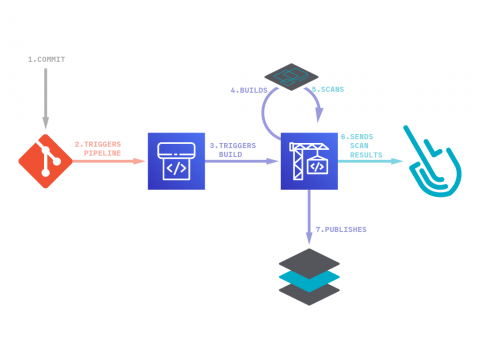
Inline Image Scanning for AWS CodePipeline and AWS CodeBuild
In this blog post you’ll learn how to set up image vulnerability scanning for AWS CodePipeline and AWS CodeBuild using Sysdig Secure DevOps Platform. AWS provides several tools for DevOps teams: CodeCommit for version control, CodeBuild for building and testing code, and CodeDeploy for automatic code deployment. The block on top of all these tools is CodePipeline that allows them to visualize and automate these different stages.
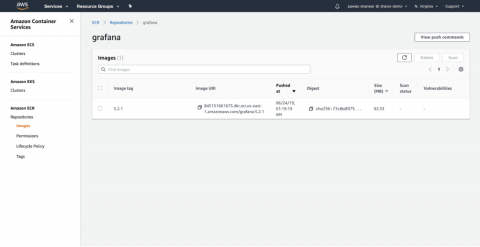
AWS ECR Scanning with Sysdig Secure
As container adoption in AWS takes off, ECR scanning is the first step towards delivering continuous security and compliance. You need to ensure you are scanning your images pulled from AWS ECR for both vulnerabilities and misconfigurations so that you don’t push applications running on AWS that are exploitable.
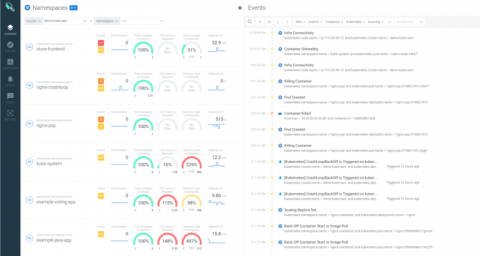
Sysdig extends security across all AWS container services
Cloud teams are increasingly adopting AWS container services to deliver applications faster at scale. Along with the roll out of cloud native architectures with containers and orchestration, what’s needed to stay on top of the security, performance and health of applications and infrastructure has shifted. At Sysdig, we’ve worked with Amazon to provide tools and integrations that help secure your Cloud Native workloads deployed across all AWS container services.
Arctic Wolf: Redefining Cybersecurity
IT Security Risk Assessment Methodology: Qualitative vs Quantitative
Formulating an IT security risk assessment methodology is a key part of building a robust information security risk management program. The two most popular types of risk assessment methodologies used by assessors are: A risk assessment is a process that aims to identify cybersecurity risks, their sources and how to mitigate them to an acceptable level of risk.