Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
%term
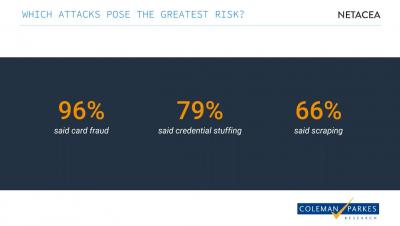
Uncovering Bots in eCommerce Netacea Webinar
What lies beneath your website traffic with Forrester Research
Gaming & Gambling Bots Featuring Lovelace Consultancy
4 Ways CASBs Differ from Cloud DLP
CASBs have traditionally been a popular option for enterprises seeking to secure their data. Both Gartner and Forrester predict that cloud security will continue to be a growing market through the end of 2023. Gartner projections foresee a 20% increase in CASB usage at large enterprises by 2022, while according to Forrester, cloud security will become a $112.7B market by 2023.
Best Practices for Security in SSH
Secure Shell (abbreviated as SSH) is a network protocol that aims to offer an extra layer of protection. In this article, we will discuss how you can ensure the security of your network using SSH. Keep reading to learn more! With the advancements in technology, many business processes we carry out today heavily relies on the internet, online tools and connected devices.
Employee PC Monitoring Software
You never have to wonder about what your employees are doing during work hours again. With Veriato, the most robust PC monitoring software on the market, you can monitor every digital move your employees make, regardless of whether they are working in the office or at home. It’s never been easier to keep track of your employees’ digital activity thanks to Veriato.
Detecting Google Cloud Platform OAuth Token Abuse Using Splunk
In a recent post by the Splunk Threat Research team, we addressed permanent and temporary token/credential abuse in AWS and how to mitigate credential exposure. With 94% of Enterprises using a cloud service, and some using at least five different cloud platforms, it’s imperative to stay ahead of threats across multicloud environments. Let’s now turn our attention to Google Cloud Platform (GCP) and how to detect and mitigate OAuth Token Abuse.
Eclipse SW360: Main Features
Over five years ago, Adrian Bridgwater wrote a Forbes article pronouncing that “If Software Is Eating The World, Then Open Source Will Chew It Up (And Swallow).” That statement is just as true today. Open source components have become a basic building block for software developers, providing them with ready-made solutions from a vast community that help them keep up with today’s speedy and frequent release cycles.
What is Emotet Malware and how is it Delivered?
Emotet originally arrived on the scene as a new banking trojan in 2014. In the past 12 months, however, it has evolved from a standalone threat into a prolific distributor of other trojans, including TrickBot, Zeus Panda Banker, IcedID, Qakbot, and Dridex.