Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Content Management
How Egnyte Got Its Engineers to Use a New Configuration System
You can build the best system in the world, but it won’t matter if no one uses it. That might sound obvious, but it’s often overlooked. Getting your users to buy into a new system is not as easy as flipping a switch. It takes planning, initiative, and reinforcement to make sure your software is broadly adopted.
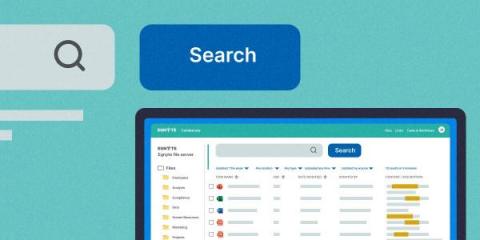
Get the Most Out of the Desktop App with Search, Recents
Egnyte users want to get the files they need as fast as possible. Less time spent scouring folders means more time doing the work that really matters, and one of the best ways to do that is with the Egnyte Desktop App. With the Egnyte Desktop App you get real-time access to all your files and folders stored in the cloud, directly from your computer.
Review and Approval Workflows
CEO Customer Spotlight with First Republic Bank
Discover PII Data in Microsoft Exchange Online With Egnyte
Your organization runs on information, and much of that information is sensitive. You need consistent governance policies to protect users and data, but just protecting files is not enough. You also need to be able to scan your documents quickly and easily to find personally identifiable information (PII). More than three-quarters of companies have files housed in email repositories, and these often contain customer PII, health records, and other sensitive information.
3 Trends in eTMF Adoption After COVID-19
The TMF Summit, a clinical documentation management conference hosted by industry observer Fierce Biotech, was held in late October in New Orleans. There was plenty of talk about familiar topics such as data quality and integrity, as well as data submission workflows and monitoring. But what stood out this year was how the pandemic continues to reshape the industry.
Why You Should Build an Agile, Integrated Construction Tech Stack
When it comes to construction technology, one size doesn’t necessarily fit all. Businesses often have different needs that require different tools to automate established processes, or standard operating procedures (SOPs). This creates a problem, however, because decision makers have to sift through the available technologies—and the depth and breadth of what processes they can cover—to find the right solution.
Defending Against Insider Threats with Egnyte
The 5 Reasons Private Equity Firms Use Egnyte
Private equity firms understand the threat of cyberattacks all too well, but they don’t always know the best way to proactively address this growing problem. According to a recent report by global consulting firm Deloitte, worldwide private equity assets under management (AUM) are anticipated to reach $5.8 trillion by 2025.