Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Snyk
Stranger Danger Live Hacking Session | Cloud Native Application Security
Intuit: Dev-First Cloud Native Application Security
Breaking Containers to Improve Security: Docker and Snyk
Snyk's new vulnerability cards - fix issues fast with a new look and feel
One of our missions at Snyk is a simple one: help developers fix things easily. We further our mission by releasing features and improvements as quickly as possible, but it’s also just as important that developers have an experience which helps them gain as much value from Snyk as possible. This includes being able to quickly understand what needs to be fixed, and making that task incredibly easy.
Snyk Code: An Introduction to Dev-First SAST
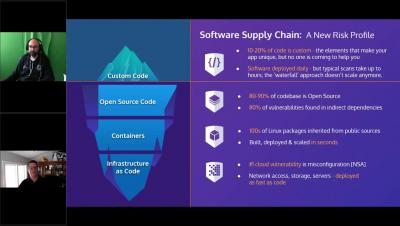
Securing your modern software supply chain
Software supply chain security concerns are more prevalent than ever. The U.S. Pentagon, Department of State, Department of Homeland Security, Microsoft, FireEye – this is just a partial list of the government agencies and companies hacked as a result of the attack on SolarWinds’ proprietary software – the Orion network monitoring program.
SolarWinds Orion Security Breach: A Shift In The Software Supply Chain Paradigm
The recent SolarWinds breach highlights a new paradigm in the Software Supply Chain. When compared simply to the code itself without any additional tools, Proprietary Code is no more secure than Open Source. By contrast, many would argue that Open Source Code is more secure due to a faster fix/patch/update cycle and the pervasive access to source code (Clarke, Dorwin, and Nash, n.d.).
Java configuration: how to prevent security misconfigurations
Java configuration is everywhere. With all the application frameworks that the Java ecosystem has, proper configuration is something that is overlooked easily. However, thinking about Java configuration can also end up in a security issue if it is done in the wrong way. We call this misconfiguration. Security misconfiguration is part of the infamous OWASP top 10 vulnerability list and has a prominent spot on place 6.