Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Networks
What is Firewall Logging and Why is it Important?
Firewall logging is an important piece of your advanced security strategy. A firewall is a security system that helps protect your computer or network from unauthorized access. One important function of a firewall is to log information about each connection attempt, including who attempted to connect and when.
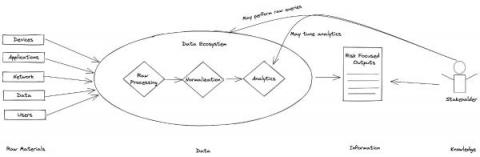
The evidence bank: leveraging security's most valuable asset
Evidence is the currency cyber defenders use to pay down security debt, balancing the value equation between adversaries and the enterprise. Defenders can use evidence proactively, identifying and protecting structural risks within our zone of control. Evidence can also be used reactively by supporting detection (re)engineering, response, and recovery activities, guiding us back to identifying and protecting structural risks.
Accelerate the Journey to Zero Trust with Forescout and Arista
Why Are Firewalls Important For Cybersecurity?
This guide has been created to explain the importance of firewalls, whitelisting and blacklisting as part of your IT security protocols in order to protect your system and improve your understanding of this topic as an IT professional. In this resource, we will also cover the key differences between using whitelists and blacklists, as well as why it is important that your security monitoring system includes ways to internally whitelist/blacklist IPs.
Choosing an RDP Client
Controlling your Windows PC remotely can open a world of possibilities; remote work, remote assistance, remote system diagnosis and network troubleshooting are just some of the advantages of using Remote Desktop Protocol or RDP. Developed by Microsoft, RDP allows you to remotely connect to another computer over a network, giving you full access to and control over the computer’s software, data and resources.
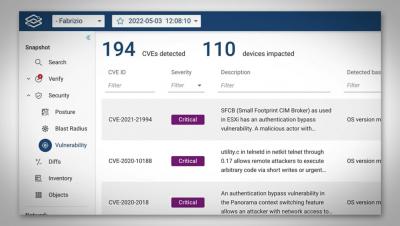
Using Forward's Vulnerability Analysis with Fabrizio Maccioni
Easily remediate the CVEs most likely to harm you using Forward Enhanced Device Vulnerability Analysis
Headline grabbing vulnerabilities, like SolarWinds and Log4Shell, target management software and end hosts, but if you search for “most exploited vulnerabilities” on Google, you will quickly learn that some of them directly target network and security devices as well as server load balancers. These are the 3 most exploited CVEs in the last couple of years: Would you be surprised to learn that network device operating systems can be vulnerable to security flaws like any other software?
What is an IT Security Network vs. a Cyber Security Network?
The terms "IT security network" and "cyber security network" are often used interchangeably, but there is a big difference between the two. An IT security network is focused on protecting your organization's computer systems and data from unauthorized access, while a cyber security network is designed to protect your entire organization from cyber attacks, including those that target your physical infrastructure.