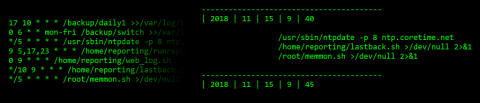
Cronview
Throughout my years working with Unix flavoured environments, one of the headaches I’ve had to deal with is cron. Don’t get me wrong, I love cron, it’s a necessity for any operation of such servers, however, there usually comes a point when the size of list reaches a critical mass that makes visualising the execution times a challenge.