Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Security
Is Your Language of Choice a Major Flaw Offender?
In volume 11 of our annual State of Software Security (SOSS) report, we uncovered some valuable nuggets of information about how you, the innovative developers of our world, can craft more secure code. For example, did you know that scanning via API improves the time to remediate 50 percent of security flaws by about 17 days, or that C++ and PHP languages have an alarmingly high number of severe security flaws and need greater attention?
The Olympics and Burner Phones: Are You Sure About the Safety of That QR Code?
As businesses try to create a contactless experience amid the coronavirus pandemic, many have turned to QR codes. We’re seeing a lot of restaurants using them to display their menus on smartphones and on receipts for a contactless pay option. Within popular apps like Snapchat and WhatsApp, QR codes are an integral part of the user experience. Users can use codes to sign into their account, exchange contact information and make money transfer.
12 Essential Tips for Keeping Your Email Safe
Hey, did you get that sketchy email? You know, the one from that malicious hacker trying to fool us into clicking on some malware? Boy, these criminals are relentless. Wait, what? You clicked on it? Uh-oh. A hypothetical scenario, but one that plays out every day in organizations across the globe — a very real scenario that provides a good reason to take a deep dive into the topic of email security. Here are some more good reasons.
Elastic on Elastic: How InfoSec deploys infrastructure and stays up-to-date with ECK
This post is part of a blog series highlighting how we embrace the solutions and features of the Elastic Stack to support our business and drive customer success. The Elastic InfoSec Security Engineering team is responsible for deploying and managing InfoSec's infrastructure and tools. At Elastic, speed, scale, and relevance is our DNA and leveraging the power of the Elastic Stack is the heart of InfoSec.
Zerologon: the most underestimated vulnerability of 2020?
Securing your businesses beyond the office perimeter
For most businesses, the corporate boundaries have expanded over time. The traditional office has now morphed into a hub-and-spoke model with an increasing number of employees working remotely. This shift to remote work isn't new. Between 2005 and 2018, there was a 173% rise in the US remote workforce. The trend spiked in 2020 when 88% of organizations worldwide encouraged remote work to flatten the pandemic's spread.
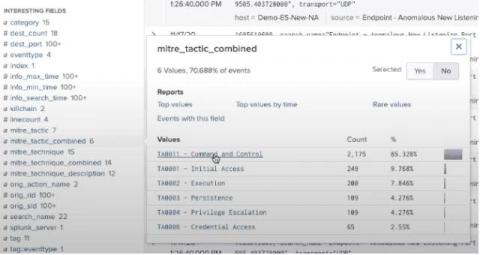
The Value of Operationalizing MITRE ATT&CK According to Splunk With Guest Speaker From IDC
The global pandemic has fueled a rapid digital transformation — and led to permanent shifts in cybersecurity. In a recent joint webinar with Bryan McAninch, senior solutions engineer at Splunk, and guest speaker Chris Kissel from IDC, "Sp(e)lunking Security with MITRE ATT&CK® featuring IDC Research," they shared seven overarching trends in cybersecurity for 2021. One notable, but foundational, trend mentioned was the need to understand risk.
Calligo launches world's first managed service to make machine learning accessible to any business
IT security under attack: A typical day in the life of an IT admin or security analyst
The job of IT admins and IT security analysts are, without a doubt, some of the most important jobs in any company. When things are running smoothly, it is easy for everyone to forget they exist. However, the moment things go askew, everyone points fingers at them. IT security professionals are expected to know everything. Most of them are self-taught and have learned on-the-job. Over time, experience has turned them into battle-hardened soldiers.