Largest Iran's Bank Allegedly Breached Exposing 47M Records Of The Customer
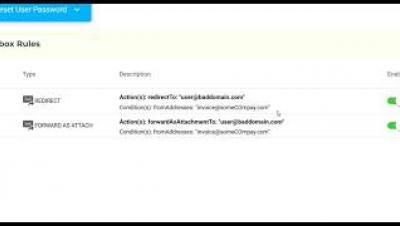
Recently, while performing a deep inspection of the dark web through Foresiet DigiRisk Platform, our Cyber Research and Support Team (FCRST) noticed, 33M records of Iran Bank were found breached and available. Our researcher has validated the data and it's very scary and has complete information including Account detail, card detail, PII information.