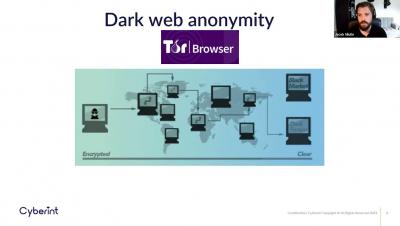
Everything You Need to Know to Improve JavaScript Security
JavaScript is a great programming tool, but JavaScript security problems can cause significant damage to organizations and their customers. To help cybersecurity professionals and software developers better understand everything they need to know to improve JavaScript security, we’ve developed a free, comprehensive e-book, The Ultimate Guide to JavaScript Security.