Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Security
Why Security Awareness Training Does Not Equal Security Behaviour Change
Is Security Awareness and Training the 2nd Class Citizen of Cyber Security?
Presenting Accurate Security Behaviour Data to the Board
What the Future of Human Risk Management Looks Like
Measure Actual Security Behaviour Change, Not training Completion
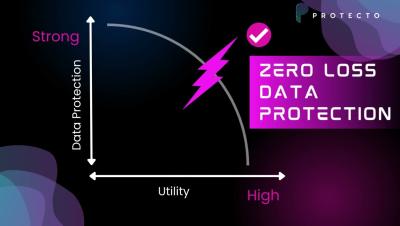
Breaking the Barrier: Introducing Zero Loss Data Protection by Protecto
IoT Device Management: A Comprehensive Guide for 2023
Imagine a world where managing thousands of connected devices is as easy as managing one. Welcome to the era of IoT device management! With the rapid growth of connected devices across various industries, IoT device management has become an essential aspect of maintaining security, efficiency, and scalability.
ManageEngine AD360 stands tall with wins at the 11th Global InfoSec Awards
The 11th annual Global InfoSec Awards, held at the RSA Conference 2023 in San Francisco, brought together over 4,300 companies vying for recognition in various categories. Among the standout performers, ManageEngine’s AD360 won prestigious accolades in four categories. Cyber Defense Magazine (CDM) hosted the Global InfoSec Awards, recognizing the most innovative and effective cybersecurity companies and products in the industry.
New Bytesafe Feature: SBOM import
We are excited to share a new Bytesafe feature that will help you manage and secure your supply chain: the ability to import Software Bill of Materials (SBOM) files into Bytesafe. This enhancement, designed with our users' needs in mind, is a significant stride towards improved software supply chain security. It offers a solution to track current and potential vulnerabilities in your dependencies without sharing your proprietary source code or other sensitive data.