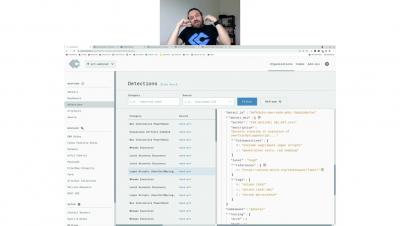
Introducing ATT&CK Detections Collector
The Splunk SURGe team loves to automate and simplify mundane tasks. Through rapid response blogs, we provide context and analysis on late breaking security events that affect everyone, not just Splunk customers. We are firm believers that through shared knowledge and experience we can help the masses better understand the threat landscape and how they can improve their security posture.