Reduce False Alerts - Automatically!
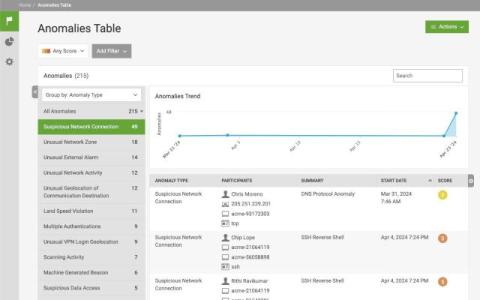
Analysts rely on User and Entity Behavior Analytics (UEBA) tools to track anomalies, investigate incidents, and respond to cybersecurity threats. However, the varying nature of user and entity behaviors across different organizations means that predetermined thresholds often fail to account for unique baselines. Even within the same environment, temporal variations can cause significant differences in monitoring signals.