Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
Advanced Active Directory attacks: Simulating domain controller behavior
There was a time when cyberattacks on identity and authentication infrastructures [like Active Directory (AD)] were immensely challenging to perform. A lot of forethought had to be put into devising a plan for the careful execution of attacks, and advanced technical knowledge of domains and networks was a requisite. Over time, with the advent of open-source pen testing tools, the knowledge gap and the complexities involved to carry out a full-scale cyberattack have narrowed drastically.
Zero Trust Architecture explained
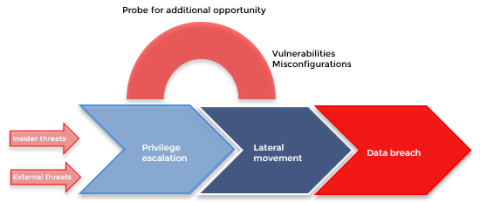
With the increase in frequency, sophistication, and cost of cyberattacks, the global focus on cybersecurity is at an all-time high. However, the goalposts for those tasked with protecting businesses have shifted. Hackers have a growing number of ways they can compromise a business and are frequently looking to move laterally within an organization, using credentialed (and often elevated) access.
Automate Fargate image scanning
Discover how to automate AWS Fargate image scanning directly in your AWS environment and block vulnerabilities from reaching production, among other threats. AWS Fargate and ECS allow you to deploy containerized workloads quickly. Fargate is even more convenient, as you don’t have to take care of the infrastructure.
AWS threat detection using CloudTrail and Sysdig Secure
Implementing AWS threat detection with Sysdig Secure takes just a few minutes. Discover how to improve the security of your cloud infrastructure using AWS CloudTrail and Sysdig Cloud Connector. With the rise of microservices and DevOps practices, a new level of dangerous actors threatens the cloud environment that governs all of your infrastructure. A malicious or inattentive cloud API request could have a sizable impact on availability, performance, and last but not least, billing.
Leaky Images: Accidental Exposure and Malware in Google Photos and Hangouts
Did you know that the default link sharing option in Google Photos allows anyone with the link to view the files and all images shared in Google Hangouts that are publicly accessible? In this edition of our leaky app series, we will cover how image link sharing in Google Hangouts and Google Photos can lead to the accidental public exposure of sensitive data. We will also look at the threat detection capabilities of Google Photos and Google Hangouts.
Shadow IT shaken with a mobile twist
If you bring up the topic of “shadow IT” to your head of IT, you will likely get a lecture about how employees need to follow protocol when using cloud cloud services so they don’t put the organization at risk. They’re not wrong. Without proper protection, unsanctioned tools can have significant consequences and unintentionally introduce security gaps.
Measuring Performance in Node.js with Performance Hooks
Measuring performance in Node.js applications can sometimes be a challenge. Do to the nature of the event loop and asynchronous code, determining the actual time a piece of code takes to execute requires tools built into the platform. First added in Node.js v8.5, as stableas of v12, the Performance Measurement APIs are stable and allow much more accurate monitoring than earlier implementations.
Best Practices for Delivering a Business-Driven Security Posture
The main focus for cybersecurity teams — moving beyond compliance — is to deliver the level of security required to manage the likelihood of a breach and the potential impact to the business. This is more effective than simply focusing on the cost of delivering security services.
Stories from the SOC - Cloud and On-site Protection
One of the benefits of having your managed detection and response (MDR) service managed by AT&T Cybersecurity is the visibility into threats from a large number of customers of all sizes and across different industries. This allows the team to take what they learn from one customer and apply it to another. Our security operation center (SOC) analysts were able to use an OTX alarm and an AWS correlation rule to discover open ports on public facing servers for two different customers in 24 hours.