Cloud security series: What are the most common cloud security challenges?
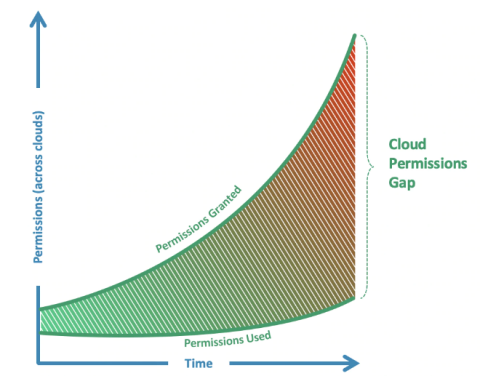
In the second of our three-part series, we highlight the most common cloud security challenges. When migrating infrastructure and services to the cloud it is vital to establish a clear strategy to avoid new security risks. As moving to the cloud can vastly widen the attack surface, it’s important to check whether current security controls will still be effective when migration is complete.