Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
Risk Assessments and Internal Controls
10 Ways to Avoid Online Shopping Scams on Cyber Monday and Beyond
Cyber Monday and the holiday shopping season are around the corner: don’t be the victim of an online shopping scam or cyber security breach. Cyber Monday is here, and the holiday shopping season is in full swing. With some of the world’s biggest brands vulnerable to a Magecart attack, you can’t be too careful with your credit card information.
What is an Enumeration Attack? How they Work + Prevention Tips
An enumeration attack is when cybercriminals use brute-force methods to check if certain data exists on a web server database. For simple enumeration attacks, this data could include usernames and passwords. More sophisticated attacks could uncover hostnames, SNMP, and DNS details, and even confirm poor network setting configurations. Every web application module that communicates with a user database could potentially become an enumeration attack vector if left unsecured.
Redirecting the Zero Trust Conversation to Build a More Robust Architecture
In a recent Tripwire survey, over 300 respondents from both private and public sectors said that implementing Zero Trust Architecture (ZTA) could materially improve cybersecurity outcomes. This result seems like a positive outcome since we don’t often get such a unanimously high confidence level in a specific security approach from survey data.
CISA Releases New Tool to Help Organizations Prevent Insider Threats
Weekly Cyber Security News 26/11/2021
A selection of this week’s more interesting vulnerability disclosures and cyber security news. For a daily selection see our twitter feed at #ionCube24. The joys of electric cars, and because you have all the gizmos at your disposal does it mean you should use them at every opportunity?
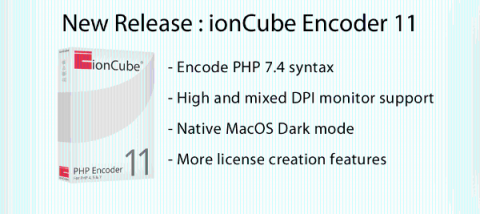
New: ionCube Encoder 11 released & our Black Friday 2021 offers
ionCube Encoder 11 is now available at ioncube.com and supports PHP 7.4 syntax encoding as well as including a range of other improvements. It also happens to be Black Friday and so we are able to offer this brand new release at a great discount!
Sophisticated Tardigrade malware launches attacks on vaccine manufacturing infrastructure
Security researchers are warning biomanufacturing facilities around the world that they are being targeted by a sophisticated new strain of malware, known as Tardigrade. The warning comes from the non-profit Bioeconomy Information Sharing and Analysis Center (BIO-ISAC) which revealed that at least two large facilities working on manufacturing bio-drugs and vaccines have been hit by the same malware this year, in what appear to be targeted attacks.
How to Make Slack HIPAA Compliant in 2022
As digital transformation continues post-COVID more organizations, including those covered by HIPAA, will seek out SaaS solutions that make collaboration easier. Fortunately more and more applications like Slack are enabling HIPAA compliant use. In early 2019 as Slack filed for its IPO, the company also updated its security page to provide details on its qualifications as a HIPAA compliant messaging app.