Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
What is Third Party Due Diligence? What You Should Know
Due diligence is one of the most important steps before starting a partnership with a third-party business, as it reveals any hidden risks or vulnerabilities that could harm your network. In this blog, we will define third-party due diligence, explore the benefits of conducting cybersecurity due diligence, and describe how to get started.
CVE-2022-0185: Kubernetes Container Escape Using Linux Kernel Exploit
On Jan. 18, 2022, researchers found a heap base buffer overflow flaw (CVE-2022-0185) in the Linux kernel (5.1-rc1+) function “legacy_parse_param” of filesystem context functionality, which allows an out-of-bounds write in kernel memory. Using this primitive, an unprivileged attacker can escalate its privilege to root, bypassing any Linux namespace restrictions.
6 Tips for Supply Chain Risk Management in 2022
Forrester recently predicted that in 2022, 60% of security incidents would involve third parties. Yikes! With such a large percentage of incidents taking place outside the confines of their organizations, corporate leaders need to know what to do to protect their business. So, here is a list of items to address to succeed at supply chain risk (SCR) management.
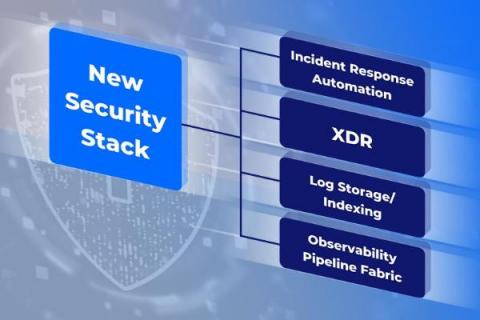
New Security Reference Stack For Modern Enterprise
ISR Q3 2021: 6 steps to reduce threat risk
The latest Internet Security Report, produced by the WatchGuard Threat Lab team, compiles analysis detailing malware evolution and trends based on data collected from 35,180 Firebox devices worldwide. Its key findings are as follows: This rate of incidents that the report has outlined for Q3 2021 does not seem to have decreased in severity in recent months. For these reasons, organizations should adopt several measures in order to be better prepared for upcoming threats.
3 Surprising Ways Ransom Attacks Could Destroy the 2022 Olympic Games
Though the level of fear of Covid 19 has diminished, there are other fears surrounding the 2022 Olympic games. Fears of telecom disruptions and ransomware attacks are founded, and the damage that could be caused has increased with the reliance on technology to broadcast the Games, which kicks off on February 4. Organizers are preparing for the kind of cyberattack that temporarily paralyzed IT systems ahead of the official opening ceremonies of the 2018 Pyeongchang Winter Olympics in South Korea.
Introducing Synthetic Adversarial Log Objects (SALO)
The SURGe team at Splunk is always exploring new methods and tools to make our lives easier. Today we’d like to share some of that work with you. Before we dive into the what and how, I’d like to briefly explain the why.
CAPTCHA Risks: More dangerous than useful?
CAPTCHA and reCAPTCHA are an ever-present component on any website that requires user interaction. But the risks of embedding CAPTCHA/reCAPTCHA plugins on a website can outweigh the benefits. Flawed code can increase the threat of client-side attacks. Who hasn’t encountered a CAPTCHA?
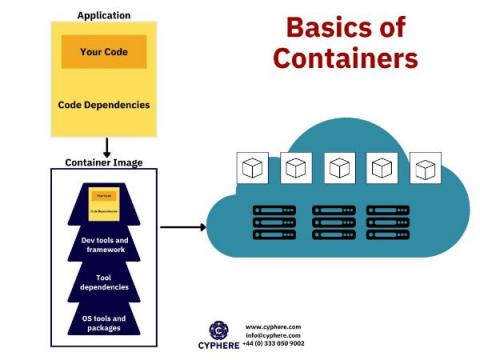
What is Container Security?
A container is defined as packaged software that contains all the code and dependencies of an application within a virtual environment so that the application can be migrated from any computing device to another. Docker container images are executable software packages that are lightweight and standalone.