What is a Reverse Proxy, How Does it Work, and What are its Benefits?
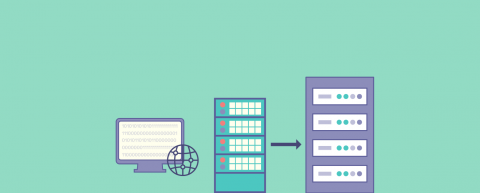
A reverse proxy is a server that sits between the client and the origin server. It accepts requests from clients and forwards them to the appropriate server. It also receives responses from the server and sends them back to the client. A reverse proxy is an essential component of web application infrastructure, providing a layer of abstraction between clients and origin servers to help optimize traffic routing and improve performance and security.