Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
7 Cybersecurity Trends for 2024
Tips for Achieving Success With a NERC CIP Audit
Electrical utilities are responsible for just about everything we do. This presents a tremendous burden on those who operate those utilities. One way these organizations offer assurance is through the audit process. While audits can generate tremendous anxiety, good planning, and tools can help make the entire process go smoothly. Moreover, these can also help to achieve positive results.
Operational Resilience: What It Is and Why It's Important
Frankly stated, operational resilience is your ability to climb the mountain, no matter the weather. Businesses now need more than a good security structure to weather the storms of AI-driven threats, APTs, cloud-based risks, and hyper-distributed environments. And more importantly, operational resilience in 2024 requires a paradigm shift. Attackers aren’t out there doing the bare minimum. As the numbers suggest, they’re getting the job done.
CRQ Journey Part 1: The Problem With Standalone Cyber Frameworks
A New Way to View Vulnerabilities: Improving Your Workflow
We are thrilled to announce the introduction of our new vulnerabilities page on assessments. This innovative update allows you to view the overall status and remediation progress of all your assets for a single assessment in one comprehensive view. We've listened to your feedback, and we believe these enhancements will bring a more streamlined and efficient approach to your vulnerability management.
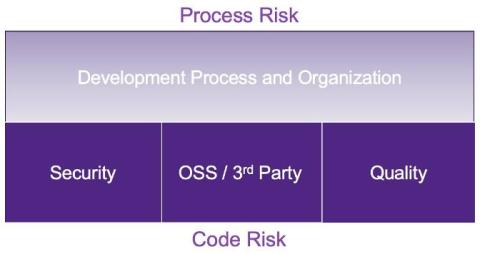
Making intelligent tradeoffs in software due diligence
Oregon Healthcare Provider Suffers Employee Email Data Breach
In Oregon, the Neuromusculoskeletal Center of the Cascades and Cascade Surgicenter collectively are “The Center.” The professionals that work there are highly trained doctors from many fields, including physiatry, occupational medicine, neurosurgical, and orthopedic care. The Center serves central Oregon at three stand-alone clinics and rural treatment at six shared clinics.
What is Cybersecurity Automation?
Fraud Risk Management: Employing KYC-as-a-Service Solutions
In an era of economic fluctuation, companies face increased vulnerabilities both internally and externally, leading to a rise in exploitation risks. The magnitude of this issue is highlighted by the $41 million in global payment fraud losses recorded in 2021, with North America and Europe being major contributors. Projections suggest a worrying trend, with potential losses reaching up to $343 billion by 2027. Addressing this growing concern necessitates a robust fraud risk management approach.