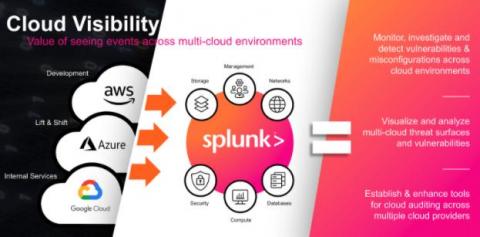
Managing Cyber Threats to Operational Technology
In the fast-paced and highly commercialized world of manufacturing, better automation creates a valuable competitive edge. The physical systems leveraged in the industry, the machinery, and the manual processes have all become more automated since the first industrial revolution. Today, smart systems that leverage advanced technologies such as machine learning and integrated IoT control are creating a next-generation industrial environment often termed 4.0.