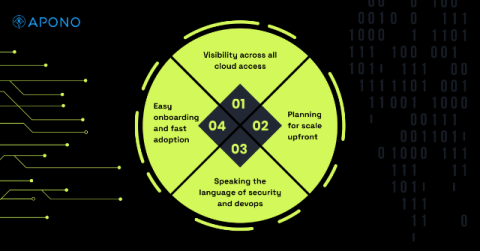
Elevating Cyber Resilience for Your Business
Protecting your business from cyber threats today means building a stronger tomorrow. As we see firsthand, the digital backdrop has grown increasingly complex, and with it, the risks businesses face daily. AI-powered threats are more sophisticated, making it critical for organizations to evolve their cybersecurity strategies.