SaaS Security Posture Management/SSPM: A Must-Have for Securing Your SaaS Applications
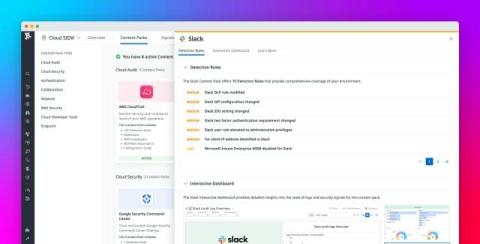
As more companies adopt Software-as-a-Service (SaaS) apps, keeping these cloud-based systems secure has become crucial. While SaaS offers convenience, scalability, and flexibility, it also introduces significant security risks. Organizations must actively monitor and control the security of their SaaS environments. SaaS Security Posture Management / SSPM is becoming an essential tool for this task.