Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
How to effectively detect and mitigate Trojan Source attacks in JavaScript codebases with ESLint
On November 1st, 2021, a public disclosure of a paper titled Trojan Source: Invisible Vulnerabilities described how malicious actors may employ unicode-based bidirectional control characters to slip malicious source code into an otherwise benign codebase. This attack relies on reviewers confusing the obfuscated malicious source code with comments.
What is a Cyber Threat? Types and Sources
A cyber threat is any kind of attack against what we consider cyber security. Cyber security is what we use to protect our computers and networks from intrusions or attacks that can be harmful to us. There are many different types of cyber threats like malware, ransomware, botnets and phishing scams etc.
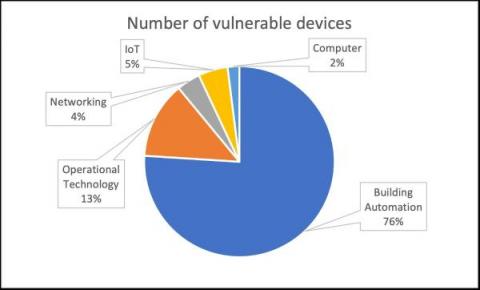
New Critical Vulnerabilities Found on Nucleus TCP/IP Stack
Forescout Research Labs, with support from Medigate Labs, have discovered a set of 13 new vulnerabilities affecting the Nucleus TCP/IP stack, which we are collectively calling NUCLEUS:13. The new vulnerabilities allow for remote code execution, denial of service, and information leak. Nucleus is used in safety-critical devices, such as anesthesia machines, patient monitors and others in healthcare.
Vendor Management Best Practices
Establishing positive vendor relationships is crucial to running a successful business. Nonetheless, vendor management has several moving parts, and you have a lot of things to keep track of. This includes who your third parties are, the services they offer, which internal policies apply to them, and what sensitive data they have access to. Without a strong foundation of vendor management best practices, vendor risks could manifest into failures that could affect business continuity.
99% of Federal Security Pros Feel the U.S. Government Must Do More to Protect Its Data and Systems
As you’ll recall, the White House published an Executive Order (EO) on Improving the Nation’s Cybersecurity back in May 2021. The EO issued several commands such as creating a Cyber Safety Review Board to lead post-incident analysis of significant security events and requiring software developers to make data about their solutions publicly known.
8 Best Practices for Data Security in Hybrid Environments
Operating in hybrid environments can get really tricky at times. As more and more organizations are moving their sensitive data to the public cloud, the need to keep this data secure and private has increased significantly over time. While handling their valuable datasets within their respective environments, companies need to ensure utmost data security and compliance to meet the regulations set by various governments.
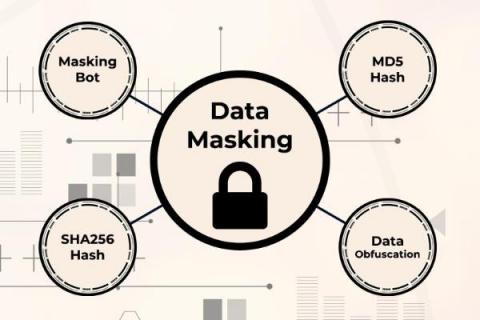
How to Easily perform Data Masking of Social Security Numbers (SSNs) in Log files or Events in 4 Ways using Data Bots
Secure sensitive files and data in Box with Nightfall's Box DLP Scanner
Storing files safely in the cloud is one of the foundations of remote work. File sharing platforms like Box were popular before the pandemic for their ease of use and collaboration between users anywhere in the world. Now that we’re living and working in a world where remote work is the norm, they’ve become essential pieces of digital infrastructure.
CMMC 2.0 Overview: What Changed?
The Cybersecurity Maturity Model Certification (CMMC) is an emerging program created to ensure cyber protection of vulnerable Federal Contract Information (FCI) and Controlled Unclassified Information (CUI) for companies within the Defense Industrial Base (DIB).