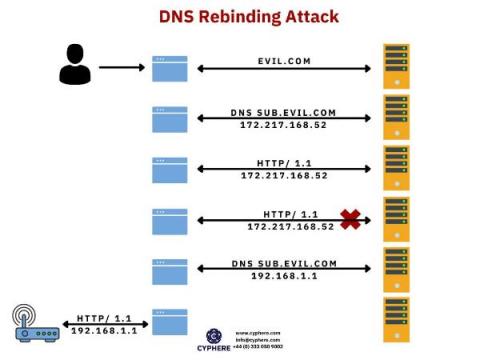
Identifying exploits and adversary tradecraft of FORMBOOK information-stealing campaign
We wanted to call out some great adjacent research from the team at Sophoslabs Uncut that was released on December 21, 2021. Research groups frequently analyze similar (or in this case, identical) campaigns through their own unique lens. This is fantastic for the security community, as the campaign gets more eyes and different perspectives applied towards the same problem.