Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
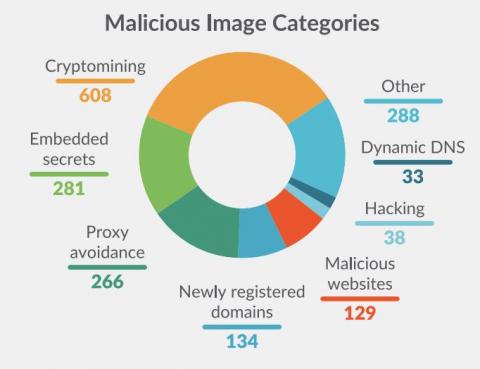
Analysis on Docker Hub malicious images: Attacks through public container images
Supply Chain attacks are not new, but this past year they received much more attention due to high profile vulnerabilities in popular dependencies. Generally, the focus has been on the dependency attack vector. This is when source code of a dependency or product is modified by a malicious actor in order to compromise anyone who uses it in their own software.
General Overview: Cyber Threats in Todays Society
Cyber threats are a big deal in today’s society. It seems like every other day, there is a new scam or cyber attack that is making the rounds. In this blog post, we will take a look at some of the biggest threats and scams that you need to be aware of. We will also discuss how to protect yourself from these attacks.
Killnet Claims Attacks Against Starlink, Whitehouse.gov, and United Kingdom Websites
Pro-Russian threat actor group Killnet claims to have launched DDoS attacks against Starlink and the United States’ government website whitehouse.gov. Starlink is a satellite internet service company operated by SpaceX. In 2019, SpaceX began launching Starlink satellites, and as of September 2022 is reported to have launched more than 3,000 satellites into low-Earth orbit (LEO).
GitHub Secrets Detection & Data Loss Prevention Guide
Environments like GitHub present data exposure risk in the form of secrets leakage and sensitive PII leaking from repositories. Read this online guide, for free, to learn about the problem of secrets exposure and leakage in GitHub, as well as how to easily implement secrets detection and scanning to prevent this risk.
How to Integrate HECVAT into VRM Programs
HECVAT (Higher Education Community Vendor Assessment Toolkit) is a security assessment questionnaire that measures the cybersecurity risk of third-party vendors for higher education institutions. It helps universities ensure that their third-party vendors have implemented proper security practices and policies, which are measured against a comprehensive list of security controls, to protect the large amounts of sensitive data and personally identifiable information (PII) they manage.
Scalable, Faster, Cheaper - Pick All for Azure Protection
Rubrik allows customers to protect their workloads like VMs, Disks, and SQL instances running on Azure. We have customers who protect a large number of Azure subscriptions through our SaaS product. We offer features like File-Level Recovery to allow customers to make faster recoveries and Storage Tiering to save on storage costs associated with the backups. To support these features, we run compute in the customer’s environment to read the data from Azure Disk snapshots.
73 Percent Of Retail Applications Contain Security Flaws, But Only A Quarter Are Fixed
Leonardo UK selects Rizikon from Crossword Cybersecurity to assist with assessment of supply chain cyber risks
ManageEngine wins at the Cybersecurity Breakthrough Awards 2022!
It gives us immense pleasure to announce that ManageEngine has been declared a winner in the Cybersecurity Breakthrough Awards 2022. ManageEngine ADAudit Plus, our IT security and compliance solution, was the winner in the User Behavior Analytics Security Solution category. The Cybersecurity Breakthrough Awards aim to recognize the top companies, products, technical innovation, and people that break through the crowded cybersecurity industry.