Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
Financial Institutions and Cybersecurity Risk: Why you need ISO27001
When it comes to law enforcement crime investigations, there is a maxim of, “follow the money”. This broadly means that if you can follow the money trail, it will eventually lead you to the perpetrator of the crime. In today’s modern society, money has now become a series of binary ones and zeros that are transferred between bank accounts without any real effort on either party, and cybercriminals are fully aware of how easy, and fragile, this process is.
LTT Attack Targets Session Cookies to Push Crypto Scam
Crypto scams are skyrocketing: In 2022, the FBI tracked an 183% year-over-year increase, driving $2.57 billion in losses. Last week, the popular YouTube channel Linus Tech Tips (LTT for short) – and two associated channels – became the latest crypto scam victim and unsuspecting accomplice.
Kroll recognised as an MDR Champion by Bloor Research
Is Clop Ransomware the New Threat to Watch?
Trustwave Partners with Intelisys to Deliver Managed Security and Consulting Services
Trustwave has inked a channel partnership deal with Intelisys, one of the nation's leading providers of technology services and solutions, that will allow its network of more than 1,700 sales partners to offer Trustwave security consulting, managed detection and response (MDR), threat hunting, co-managed SOC, database security, and email security to their client base.
How often should security audits be?
In today’s digital world, it’s no surprise that cyberattacks are becoming more frequent and intense. Enterprises worldwide are trying to defend themselves against attacks such as ransomware, phishing, distributed denial of service and more. In this challenging cybersecurity landscape, now is the time for companies to prioritize security audits. What are cybersecurity audits and how often should they be to remain safe in the threatening IT world?
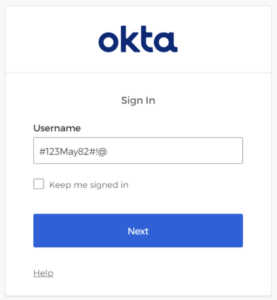
How Continuous Threat Hunting Addresses Potential Okta Password Exposure Via Failed Login Attempts
Using Egnyte's Intelligent Document Classification to Quickly Locate and Manage AEC Documents
Architecture, engineering, and construction (AEC) professionals know the importance of keeping their documents organized, but often find themselves racing against time to locate needed materials. With this in mind, Egnyte announces its new AEC-specific document classification feature that will automate and simplify the classification and discovery of essential files like drawings, specifications, RFIs, and submittals.
CVE-2023-21716: Microsoft Word RCE Vulnerability
In the February 2023 Patch Tuesday, Microsoft fixed a remote code execution vulnerability in Microsoft Word, tracked as CVE-2023-21716. The vulnerability is critical, having a CVSS score of 9.8 out of 10, and could allow an attacker to execute code with the same privileges as the victim through rich text format (RTF) documents.