Securing Our World
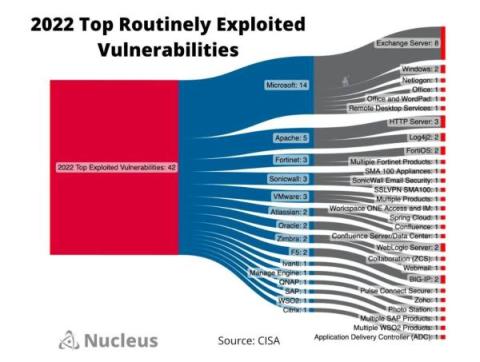
October is Cybersecurity Awareness Month, a dedicated month for the public and private sectors to work together to raise awareness about the importance of cybersecurity. And this year’s theme, “Secure Our World,” couldn’t be more timely. With the growing number of cyberattacks worldwide, it’s becoming increasingly apparent that critical infrastructure is at risk.