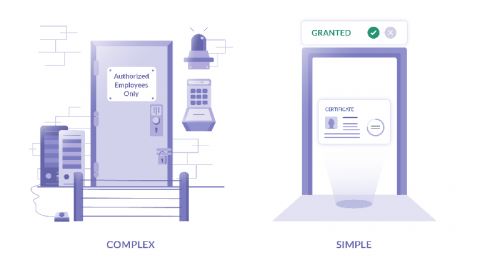
The Changing Face of Email Security
With the rise of remote work, especially in recent months, and the number of net-connected devices rising all the time, email is more relevant as ever. Indeed, as a form of unobtrusive communication and document sharing, email has pretty much cemented its position as the go-to tool for businesses of all sizes. Unfortunately, being the popular kid in school is not always a good thing – for a start, it has a way of making you look like an easy way in.