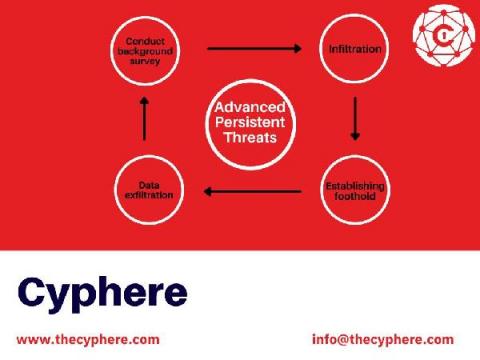
How identity management and compliance with security standards can help prevent sensitive data leakage
Cyber criminals can gain access to sensitive data through unauthorized access. Learn how to use security standards to set up preventative measures.