Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
Meeting PCI DSS Third-Party Risk Requirements
Organizations must enact effective third-party risk management (TPRM) programs to ensure their vendors fulfill cybersecurity requirements. Otherwise, they risk carrying the financial and reputational harm caused by customer data breaches. The PCI DSS standard covers aspects of third-party risk management as it's applicable to all organizations that process credit card data, especially the heavily regulated finance industry.
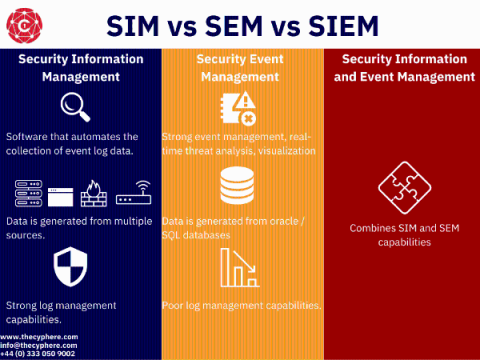
What is SIEM? A guide to cyber Security Information and Event Management
Security information and event management refer to Security Information Management (SIM) and Security Event Management (SEM) through a single pane of glass. SIEM solutions are used by security analysts to monitor any potential threats within the infrastructure of their organisation.
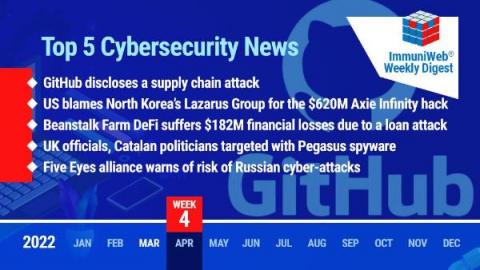
GitHub: Hackers Breached Multiple Orgs Using Stolen OAuth User Tokens
Read also: the US blames North Korea’s Lazarus Group for the $620M Axie Infinity hack, Beanstalk Farm suffers $182 million financial losses due to a cyber-attack, and more.
Network attacks, the protagonists of the latest Internet Security Report
Today’s threat landscape is evolving rapidly. Attackers are constantly adjusting their tactics and finding new ways to infiltrate organizations with increasingly sophisticated attacks to steal valuable data. As such, businesses and IT professionals must remain up to date on the industry’s latest threat intelligence in order to better understand the current state of this cybersecurity landscape and know their enemies to shore up defenses.
Choosing the Right Metadata Store: Part 3
Part 1 of this series covered the challenges Rubrik initially faced with its distributed database. Our applications had become quite complex to work around some of these challenges. Part 2 of this series covered how we chose a new distributed database (CockroachDB), and how we performed the migration. Next, we will dive into some of the challenges we faced after migrating to CockroachDB and how we developed on top of CockroachDB to mitigate them.
5 tips for securing PHP Laravel
Developer-centric Laravel is often described as “the PHP framework for web artisans.” It’s one of the most used frameworks within the PHP ecosystem, with an extensive community and a wide array of sub-branches dedicated to application development of all kinds. With version 1.0 launched in 2011, Laravel currently powers the websites of global companies like 9GAG, BBC, and Pfizer.
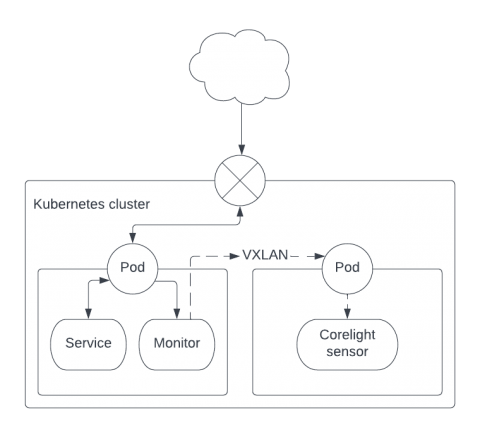
Sidecars for network monitoring
Monitoring container traffic and extracting rich security-centric metadata provides SOC analysts an inviolable source of truth for threat detection and incident investigation. This data complements the deep visibility provided by container agents and broad visibility through monitoring audit logs.
Detecting Windows NFS Portmap vulnerabilities
This month, Microsoft announced two vulnerabilities in portmap, which is part of ONC RPC, on Windows systems. This blog will discuss Zeek detection packages for CVE-2022-24491 and CVE-2022-24497 developed by Corelight Labs.
LemonDuck Targets Docker for Cryptomining Operations
The recent cryptocurrency boom has driven crypto prices through the roof in the last couple of years. As a result, cryptomining activities have increased significantly as attackers are looking to get immediate monetary compensation. According to the Google Threat Horizon report published Nov. 29, 2021, 86% of compromised Google Cloud instances were used to perform cryptocurrency mining.