You Bet Your Lsass: Hunting LSASS Access
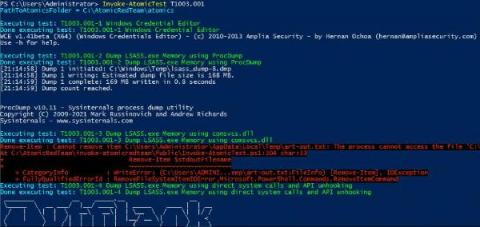
One of the most commonly used techniques is to dump credentials after gaining initial access. Adversaries will use one of many ways, but most commonly Mimikatz is used. Whether it be with PowerShell Invoke-Mimikatz, Cobalt Strike’s Mimikatz implementation, or a custom version. All of these methods have a commonality: targeting LSASS.