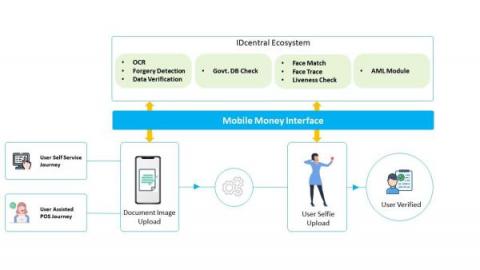
Tips for Managing Unstructured Data Security
All information is an attractive target for bad actors, but some is inherently more valuable than others. State-sponsored and hacktivist attacks constantly probe enterprise networks seeking to identify the location of sensitive information. Attackers historically targeted core enterprise systems but as the defenses for those systems have matured, attackers now target the same information but in less secured unstructured (broadly speaking, file and email based) repositories.