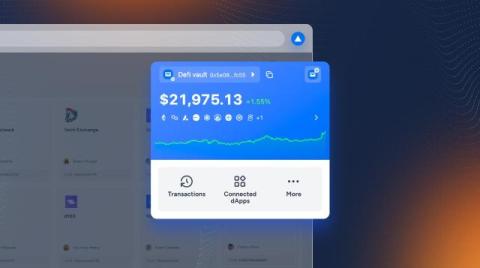
Fireblocks' new Browser Extension simplifies on-chain experience
Today, we are excited to announce our enhanced Browser Extension, providing seamless connectivity to dApps on over 30 EVM blockchains – with the security of Fireblocks MPC-CMP, Governance and Policy Engine, and DeFi threat detection capabilities. The new Browser Extension leverages components from Rabby Wallet open source, enabling customers to enjoy Fireblocks security with the intuitive Rabby interface and expansive dApp connectivity.