Vulnerability Research: Here's How it Works at Mend
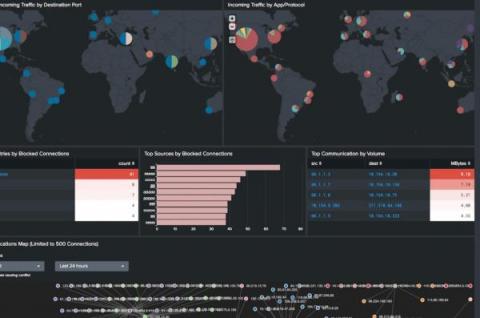
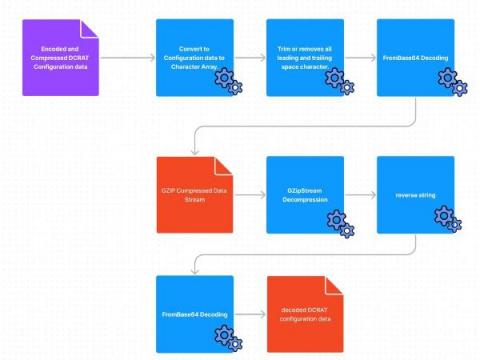
There are many types of security research, from digging into malware to discovering the latest DDoS attack vectors. At Mend, vulnerability research is a primary focus for our research team, but even that area has many different avenues to pursue. For example, we tend to focus on open source vulnerabilities, so it is quite unlikely that you’ll see us doing reverse engineering and trying to understand assembly code.