Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
Overview of the Cyber Weapons Used in the Ukraine - Russia War
Observing the ongoing conflict between Russia and Ukraine, we can clearly see that cyberattacks leveraging malware are an important part of modern hybrid war strategy. While conventional warfare is conducted on the battlefield and limited by several factors, cyber warfare continues in cyber space, offering the chance to infiltrate and damage targets far behind the frontlines. Russia utilized cyberattacks during the initial phase of the invasion in February.
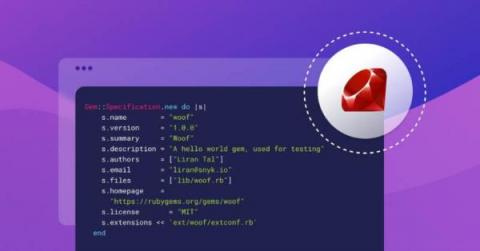
Ruby gem installations can expose you to lockfile injection attacks
In this post, we’ll look at the security blindspots of lockfile injection that a Ruby gem might expose via its Gemfile.lock. As a prelude to that, we will open up with a brief introduction to Ruby and third-party dependencies management around RubyGems and Bundler. Web developers often work on Ruby projects, but are mostly referring to them as the popular open source web application framework Ruby on Rails.
The Top 5 Most Dangerous Cyber Attacks of all Time
Cyber attacks are on the rise, and they show no signs of slowing down. In fact, many experts believe that we are only seeing the tip of the iceberg when it comes to cybercrime. As businesses continue to move their operations online, they become increasingly vulnerable to cyberattacks. In this blog post, we will take a look at the five most dangerous cyberattacks in history. These attacks have caused billions of dollars in damage and affected millions.
Stay Vigilant: How Cloud Interconnectivity Is Amplifying the Effects of Phishing
It seems like every week another household brand announces that they’ve been the victim of a data breach. Recently, cloud communications company Twilio announced that its internal systems were breached after attackers obtained employee credentials using an SMS phishing attack. Around the same time, Cloudflare, a content delivery network and DDoS mitigation company, reported that its employees were also targeted but their systems were not compromised.
Three Cases of Hacked IoT Devices
According to Gartner, 20 percent of organizations have experienced at least one attack on IoT tech in the past three years. Unsecured network connections with Internet access compromise data privacy. Through them, third parties can gain remote control over the device.
What is a Spoofing Attack and How Can You Prevent Them?
CrowdStrike Introduces Industry's First AI-Powered Indicators of Attack for CrowdStrike Falcon Platform to Uncover the Most Advanced Attacks
How small businesses can defend against common cybersecurity attacks
Managing a small business can often feel like having 100 tabs open at once. Between handling client relations, organising taxes, and keeping up with day-to-day operations, cybersecurity (particularly data security) tends to fall along the wayside. Not because business owners don’t care, but because there is simply too much to care about. For small businesses, priorities often lie with directing their resources toward creating sustainable revenue streams.
Introducing AI-Powered Indicators of Attack: Predict and Stop Threats Faster Than Ever
CrowdStrike today unveiled the next evolution of CrowdStrike’s industry-first IOAs: artificial intelligence (AI)-powered IOAs.