Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
Latest News
Predict the Future! A universal approach to detecting malicious PowerShell activity
So, here’s the deal with AntiVirus software these days: It’s mostly playing catch-up with super-fast athletes — the malware guys. Traditional AV software is like old-school detectives who need a picture (or, in this case, a ‘signature’) of the bad guys to know who they’re chasing. The trouble is, these malware creators are quite sneaky — constantly changing their look and creating new disguises faster than AntiVirus can keep up with their photos.
CTI Roundup: TA4557, OAuth Cryptomining, and the China-based KEYPLUG backdoor
TA4557 targets recruiters via email, threat actors use OAuth apps to automate BEC and cryptomining attacks, and researchers discover Sandman APT’s connection to the China-based KEYPLUG backdoor.
TEMU phishing attacks using spyware up 112% in the run up to Christmas
As the most downloaded app in the world right now, the number of TEMU impersonation emails has increased by 112% since October 1st, 2023. As discounts and spending-based reward coupons form a substantial part of TEMU’s awareness campaigns, the company is reportedly spending $2bn annually on marketing. As the brand continues to grow in popularity, cybercriminals are increasingly leveraging it to lend authenticity to their spoofing attempts.
"Mr. Anon" Infostealer Attacks Start with a Fake Hotel Booking Query Email
This new attack is pretty simple to spot on the front, but should it be successful in launching its’ malicious code, it’s going to take its’ victims for everything of value they have on their computer. The new Mr. Anon infostealer captures much more than just browser caches and passwords. It also uses basic social engineering tactics that prove to be effective enough to make attacks successful.
An Analysis of Menorah Malware
SecurityScorecard is analyzing a phishing campaign that deployed the Menorah malware, which is taking aim at users in the Middle East. This sophisticated campaign is being mounted by the threat actor group tracked as APT34, which is linked to Iran. This group is known for its focus on collecting sensitive intelligence and taking on high-profile targets across the Middle East including critical infrastructure and telecommunications entities.
TargetCompany Ransomware Group AKA Mallox: A Rapid Evolution
A Look at the Nim-based Campaign Using Microsoft Word Docs to Impersonate the Nepali Government
Threat actors often employ stealthy attack techniques to elude detection and stay under the defender’s radar. One way they do so is by using uncommon programming languages to develop malware. Using an uncommon programming language to develop malware provides several benefits, including: Netskope recently analyzed a malicious backdoor written in Nim, which is a relatively new programming language.
Play Ransomware: SafeBreach Coverage for US-CERT Alert (AA23-352A)
On December 18th, the Federal Bureau of Investigation (FBI), Cybersecurity and Infrastructure Security Agency (CISA), and Australian Signals Directorate’s Australian Cyber Security Centre (ASD’s ACSC) issued an urgent advisory to highlight the ongoing malicious activities being conducted by the Play ransomware group.
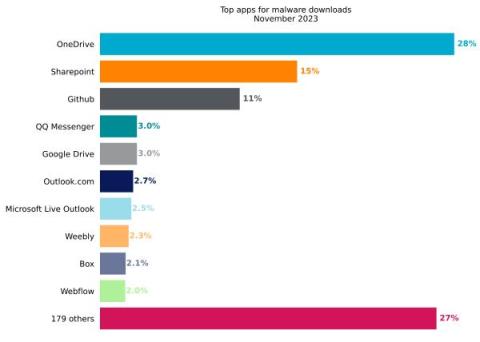
Netskope Threat Labs Stats for November 2023
Netskope Threat Labs publishes a monthly summary blog post of the top threats we are tracking on the Netskope platform. The purpose of this post is to provide strategic, actionable intelligence on active threats against enterprise users worldwide.