AsyncRAT: Using Fully Undetected Downloader
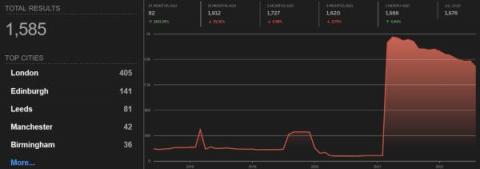
AsyncRAT is an open-source remote administration tool released on GitHub in January 2019. It’s designed to remotely control computers via encrypted connection, providing complete control via functionalities such as: Although the official GitHub repository contains a legal disclaimer, AsyncRAT is popularly used by attackers and even some APT groups. Netskope Threat Labs recently came across a FUD (Fully Undetected) Batch script which is downloading AsyncRAT from an Amazon S3 Bucket.