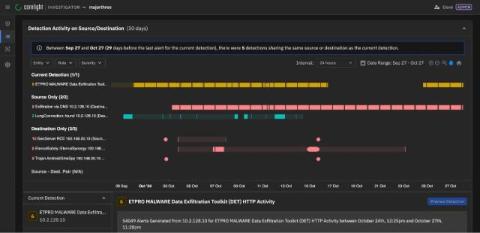
This year's resolution: remove nosey apps from your device
Some apps are plain greedy—like a stranger you invite for a meal who insists on ordering everything expensive on the menu. Except instead of a rib eye, pasta, and chocolate soufflé, it’s your data they’re collecting. Here’s what you can do to set some boundaries and reclaim your privacy in 2025.