Detecting Storm-0558 using Corelight evidence
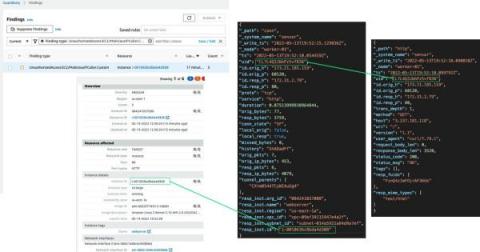
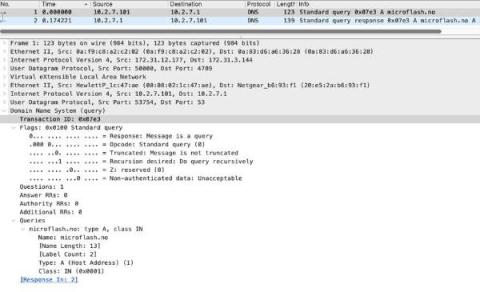
While there have been many intrusions, compromises, breaches, and incidents that have made news in the IT and InfoSec industries throughout 2022 and into this year, when events or threats like Storm-0558 gain coverage by mainstream media, we often get questions about Corelight’s ability to detect threats through our sensors, products & platform.