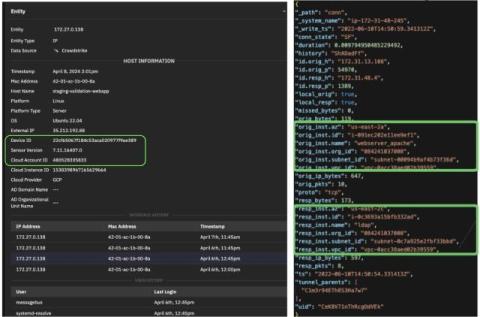
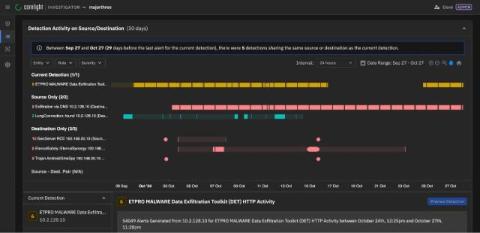
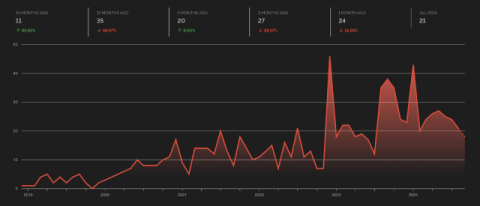
Corelight delivers data aggregation to reduce SIEM ingest by 50-80% compared to legacy network security monitoring tools
According to Forrester Research, “How do we reduce our SIEM ingest costs?” is one of the top inquiries they receive from clients. Many security organizations rely on SIEMs for their detection, investigation, and response workflows, ingesting critical security information and events to detect and respond to threats.