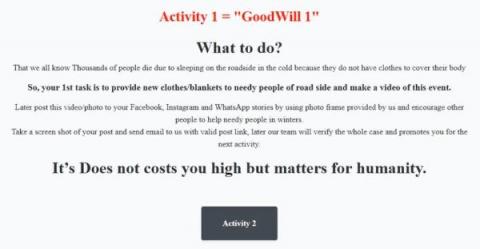
GoodWill Ransomware? Or Just Another Jasmin Variant?
In March 2022, researchers spotted a new ransomware family named GoodWill, with a new method to collect the ransom. Instead of requesting payment through crypto coins like other threats such as Night Sky or Hive, GoodWill requests that its victims help vulnerable people by following a sequence of steps, such as donating clothes, feeding less fortunate children, or providing financial assistance to hospital patients.