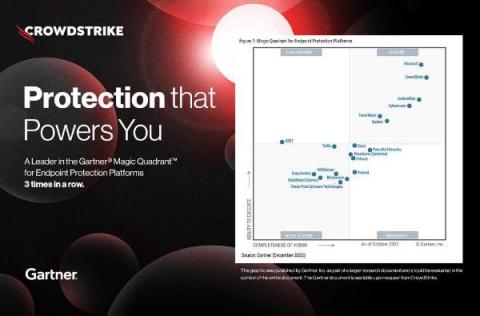
CrowdStrike's Artificial Intelligence Tooling Uses Similarity Search to Analyze Script-Based Malware Attack Techniques
According to the AV-TEST Institute, more than 1 billion strains of malware have been created, and more than 500,00 new pieces of malware are detected every day. One of the main reasons for this rapid growth is that malware creators frequently reuse source code. They modify existing malware to meet the specific objectives of an attack campaign or to avoid signature-based detection.