GKE security using Falco, Pub/Sub and Cloud Functions
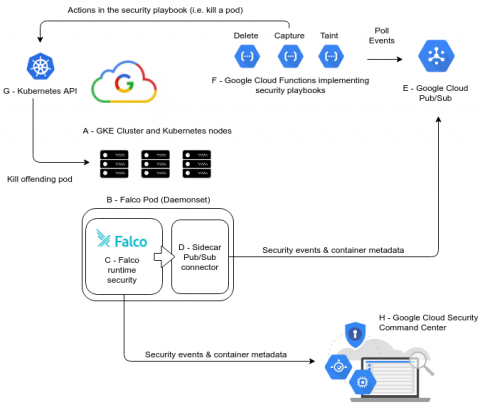
In this blogpost we will demonstrate how to build a complete GKE security stack for anomaly detection and to prevent container runtime security threats. We will integrate Falco runtime security engine with Google Cloud Functions and Pub/Sub.