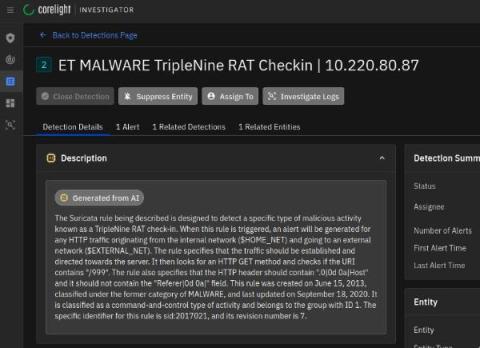
How It Works: Securing Gaming Servers From Cyber Threats
Whether you're a player or developer, you want gaming servers to stay secure. Unfortunately this is getting harder by the day, since malicious actors are always inventing new ways to cause chaos. You might be aware of the basic measures that are used to keep the infrastructure that supports top tier online experiences out of harm's way. But today's hackers are too cunning to get held back by these.