Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
April 2023
Micro Lesson: Cloud SIEM Global Intelligence for Security Insights
CS Brown Bag 4 25 Observability
Building a cybersecurity plan for the State and Local Cybersecurity Grant Program (SLCGP)
People or AI?
Security teams are faced with relentless cyberattacks, and they cannot engineer defenses fast enough. SOC teams face limited visibility, insufficient context, and the inability to identify the threats that matter. Analysts are even more burned out, switching from tool to tool, frantically trying to make sense of what they are seeing.
Enhance SOC workflows with Elastic Security and Recorded Future threat intelligence
US National Security Deep Dive Pillars 2 and 3: Dismantle Threats and Shape Market Forces
Last time we looked at The US National Security Strategy Pillar 1: Defend Critical Infrastructure. Today, we are looking at Pillar 2: Disrupt and Dismantle Threat Actors and Pillar 3: Shape Market Forces to Drive Security Resilience. Preventing the attacks in Pillar 1 would not be necessary if the attackers were taken off the board.
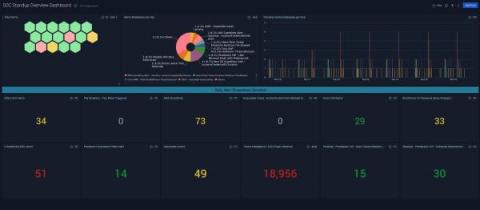
How using Cloud SIEM dashboards and metrics for daily standups improves SOC efficiency
Beyond the build: Why runtime security is critical for container protection
Threat Hunting vs Incident Response for Cyber Resilience
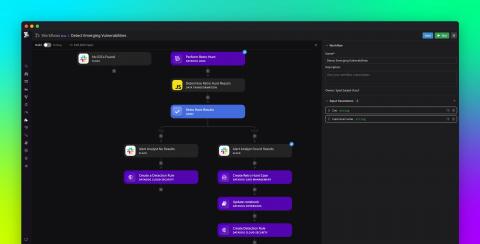
Automate common security tasks and stay ahead of threats with Datadog Workflows and Cloud SIEM
Detecting and remediating security threats is a constantly evolving concern for modern DevSecOps and security operations center (SOC) teams. Moreover, manually investigating and responding to vulnerabilities and threats is time-consuming, laborious, and knowledge-intensive.
Brown Bag Apr 18, 2023 - Security - Entity Groups
US National Cybersecurity Strategy Deep Dive: Defend Critical Infrastructure
This is the first post in a series on the pillars outlined in the new US National Cybersecurity Strategy. I review each pillar in turn, and then discuss how services such as Devo can help address the challenges outlined in that pillar.
geeks+gurus: Get real about cyber resilience
Threat Detection and Response: 5 Log Management Best Practices
Demystifying Elastic Security for Cloud and its capabilities
What is XDR? Is the security impact real or hyped?
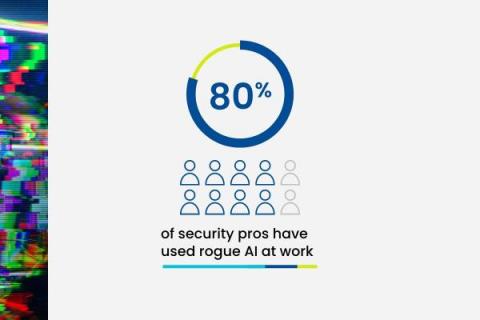
Rogue AI is Your New Insider Threat
When ChatGPT debuted in November 2022, it ushered in new points of view and sentiments around AI adoption. Workers from nearly every industry started to reimagine how they could accomplish daily tasks and execute their work — and the cybersecurity industry was no exception. Like shadow IT, new rogue AI tools — meaning AI tools that employees are adopting unbeknownst to the organization they work for — can pose security risks to your organization.