Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
May 2023
Freedom to Innovate: Data Privacy Methods
Coast Capital Savings Credit Union: Meeting Canadian Regulatory Standards for Compliance with Protegrity
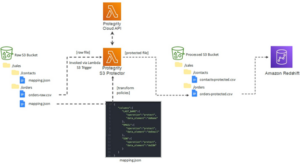
One of Canada’s largest credit unions, Coast Capital Savings Credit Union (CSS), with over 50 branches across the country, needed to protect critical PII data stored in their AWS cloud environments, Amazon Redshift, AWS EMR, and AWS S3. CSS had to meet Canadian regulatory standards for compliance in 2021, including the Personal Information Electronic Documents Act (PIPEDA), along with a data transformation initiative surrounding its architecture.
Privacy is Power: The Value of Training for Modern Data Protection
We’ve all seen it in the movies: The chief of security declares that no one could ever steal the “Famous Jewel” because it’s protected by thick glass, an impenetrable system of motion-detecting lasers, and, finally, a weight-sensitive sensor. Cut to the next scene, where a thief, dressed in sleek black, zip-lines from an open skylight, shorts the lasers, scores the glass, and with split-second timing, swaps the jewel for a replica of equal weight.