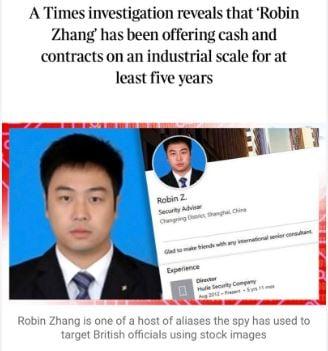
Customers of Cryptocurrency FTX are Target of Phishing Emails
Customers of the bankrupt cryptocurrency exchange FTX are already receiving phishing emails following a breach of personal data held by several crypto companies, CoinDesk reports. The customer data was leaked after a T-Mobile employee fell for a SIM swapping attack and granted a threat actor access to an account belonging to an employee of financial advisory firm Kroll.