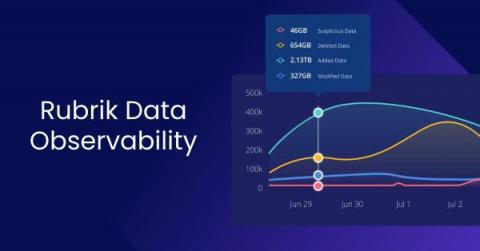
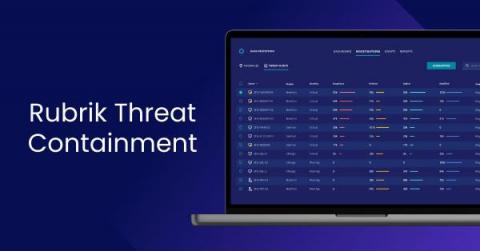
What Does Defense-in-depth Mean and How Does it Bring Infrastructure and Data Security Together?
With the rise of ransomware and cyber attacks, the term defense-in-depth has risen to the forefront, but what exactly does it mean? At its core, defense-in-depth is a protection mechanism for network security–an approach that involves layering or using multiple controls in series to protect against possible threats. This layered concept provides multiple redundancies in the event systems and data are compromised.