Security | Threat Detection | Cyberattacks | DevSecOps | Compliance
January 2022
Interview with a Hacker How are Attackers Targeting Mobile Devices
Critical Requirements for Mobile Security
0:00 Opening
6:06 What is Zero Trust?
11:48 Zero Trust workforce on mobile devices
14:57 Enabling Phishing protection on mobile
26:10 Vulnerability management for devices and applications
33:05 Ability to hunt for threats on mobile
43:45 Critical capabilities for comprhensive security
45:20 Q&A
Apps Under Attack - What You Need To Know
0:00 Opening
4:50 What mobile threats are out there?
11:20 Lookout Mobile App solution
13:35 Lookout Threat Discoveries
23:57 Banking Trojans
25:54 Strandhogg
28:40 Detecting Malware
35:36 How does Lookout protect mobile?
Critical Capabilities for Mobile Vulnerability Management
Protecting Mobile Point of Sale and Financial Apps From Cyber Breaches
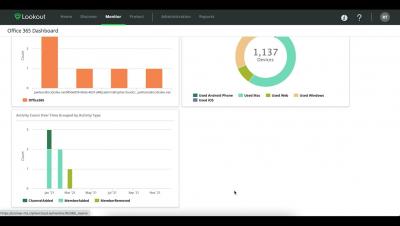
Microsoft Integration for a secure mobile workforce
Where does mobile fit into security frameworks
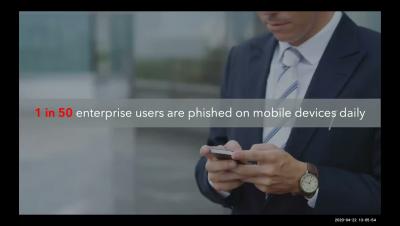
Phishing Threats in Mobile-enabled world
Steps to Stay Ahead of Risks and Protect Data Privacy
Technology has advanced our world in countless ways. Every day we bank, shop, conduct business and exchange photos and messages with family and friends online. While digital devices and services offer great convenience, they also pose risks to our data and privacy as the separation between our offline and online lives converges. Data Privacy Week, spanning January 24-28, serves as an important reminder of the importance of protecting our privacy and safeguarding personal information.
How to Reduce Risk and Secure Data With Security Service Edge (SSE)
There’s a new acronym in town: SSE, which stands for Security Service Edge. If this looks mighty similar to Secure Access Service Edge (SASE), it’s because they are closely related.
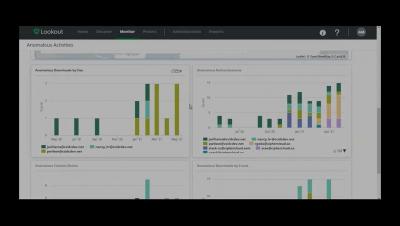
How to threat hunt with mobile EDR
Mobile threats are evolving. Is your security?
Modernizing Government Cybersecurity with Zero Trust
Lookout CASB Use Case Demonstration
Get to Know Lookout
How a Large Financial Services Firm Protects Against Data Leakage with Lookout Secure Email Gateway
Regardless of the industry or organization, corporate email is the main cause of unauthorized and accidental data leaks. Employees are constantly sending emails to external parties that may contain sensitive company data, personally identifiable information (PII), trade secrets and other intellectual property.
Best practices for a successful SASE deployment
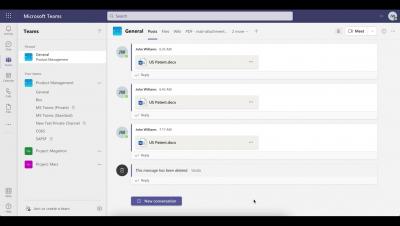
Lookout CASB - Gain insight into user and data activity within Microsoft Teams
Lookout CASB - Deny Upload to Personal Tenant in Microsoft Teams
Lookout CASB - Requiring Authentication for Sensitive Downloads in Microsoft Teams
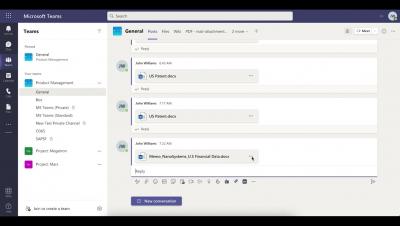
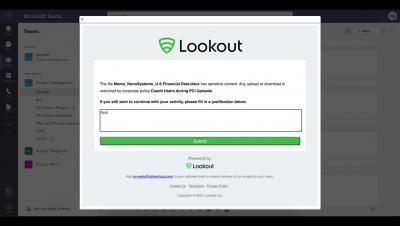
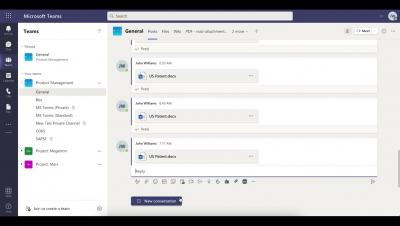
Lookout CASB - Requiring Justification for Uploading Sensitive Data in Microsoft Teams
Lookout CASB - Detection and Classification of Sensitive Data in Microsoft Teams
Pandemic-related cyber threats will persist
Mobile malware will become (even more of) a business
Endpoint Enigma | Is 2022 the Beginning of the End of On-Prem Security?
Endpoint Enigma | Let's Get Real About Zero Trust: How To Assess Your Security Posture
Your Data is Everywhere: Here are the Critical Capabilities of a Modern Data Loss Prevention (DLP)
In some ways, IT teams had a great life in the early 2000s. Data was stored inside data centers and accessed through known ingress and egress points like a castle with a limited number of gates. As a result, organizations had control over exactly whom and what devices could access company data. This is no longer the case. With users accessing cloud applications with whatever networks and devices are at their disposal, those defense mechanisms have become inadequate.
Understanding Monetary Authority of Singapore's (MAS) Guidance: Safeguarding Your Financial Institution's Cloud Environment
As a major financial hub in Asia and globally, Singapore is very aware of the challenges facing the financial industry, especially the accelerated digital transformation that stemmed from the COVID-19 pandemic. In response to the sector’s increased exposure to cloud technology, the Monetary Authority of Singapore (MAS) has released a guideline to address cybersecurity risks associated with the adoption of public clouds.
Behind the Buzzword: Four Ways to Assess Your Zero Trust Security Posture
With just about everything delivered from the cloud these days, employees can now collaborate and access what they need from anywhere and on any device. While this newfound flexibility has changed the way we think about productivity, it has also created new cybersecurity challenges for organizations. Historically, enterprise data was stored inside data centers and guarded by perimeter-based security tools.