The Common Cloud Misconfigurations That Lead to Cloud Data Breaches
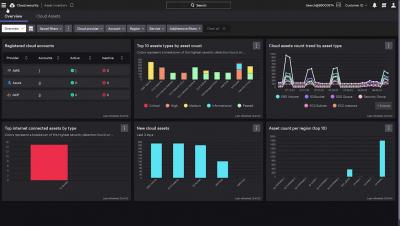
The cloud has become the new battleground for adversary activity: CrowdStrike observed a 95% increase in cloud exploitation from 2021 to 2022 and a 288% jump in cases involving threat actors directly targeting the cloud. Defending your cloud environment requires understanding how threat actors operate: how they’re breaking in and moving laterally, which resources they target and how they evade detection.